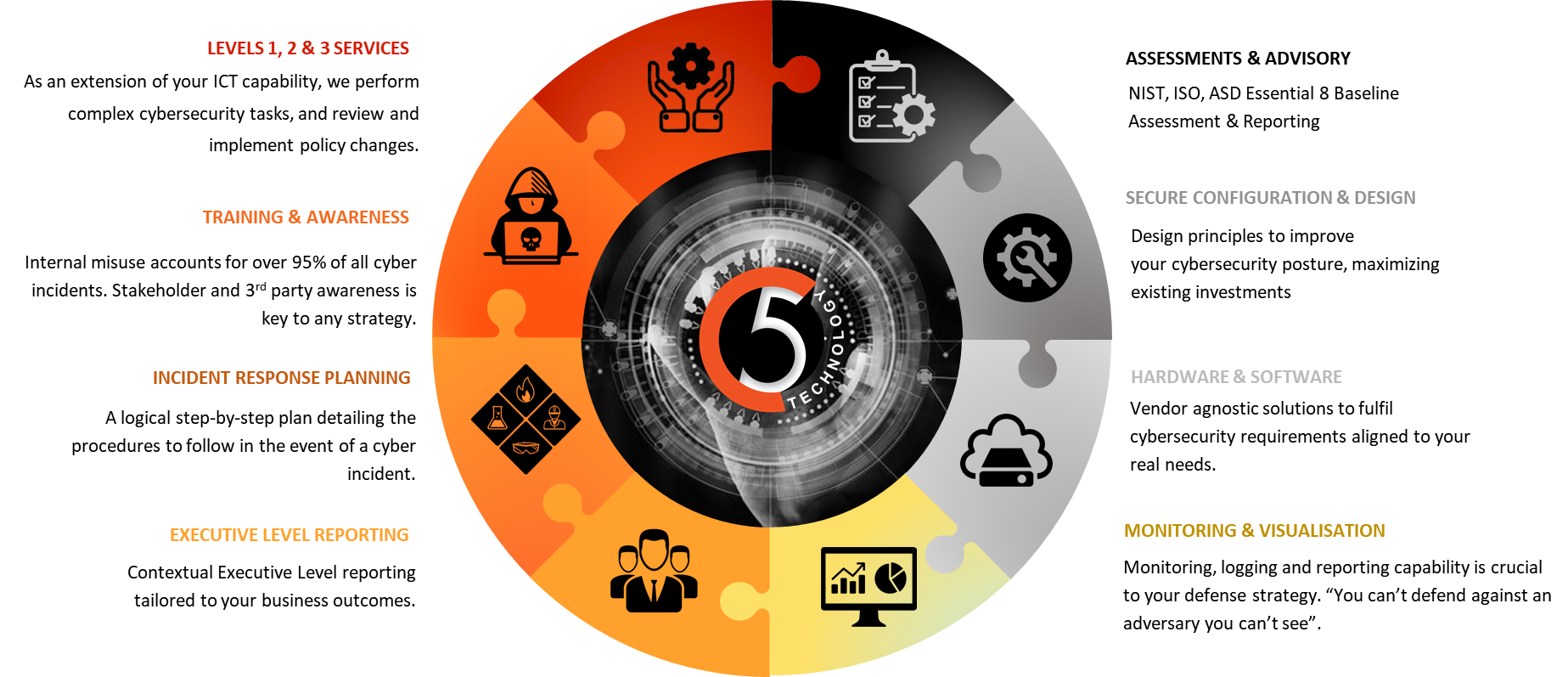
As part of understanding and actively managing your cyber security threat position, specifically your ability to prevent attacks and limit the impact of any cyber attacks, you should be assessing your organisation’s position against a Cyber Security best practice framework such as NIST or the Australian Government’s Essential 8.
As part of the C5 Technology Cyber Security model, we provide assessments of an organisations Cyber Security position relative to the Essential Eight framework.
Essential Eight
The Essential Eight is an Australian Cyber Security framework developed by the Australian Government’s Australian Cyber Security Centre (ACSC). Developed as part of a suite of prioritised strategies to mitigate Cyber Security Incidents and help organisations protect themselves against various cyber threats. The most effective of these mitigation strategies are the Essential Eight.
The framework, published in 2017, with significant updates in July 2021, sets out 8 key security controls that aim to help protect Australian businesses from cyberattacks today.
These eight strategies are divided across three primary objectives – prevent attacks, limit attack impact, and data availability.
- Objective 1: Prevent Cyberattacks
-
- Patch application vulnerabilities
- Application control
- User application hardening
- Configuring MS Office Macro settings
- Objective 2: Limit the Impact of Cyberattacks
-
- Patch operating system vulnerabilities
- Restrict Admin access
- Implement Multi-Factor Authentication (MFA)
- Objective 3: Data Recovery and System Availability
- Daily backups.
The Australian Cyber Security Centre (ACSC) established a three-tier maturity model for the Essential Eight to help businesses protect themselves against cyber threats.
- Maturity Level Zero: Not yet aligned to the intent of the mitigation strategy
- Maturity Level One: Partly aligned with the intent of the mitigation strategy
- Maturity Level Two: Mostly aligned with the intent of the mitigation strategy
- Maturity Level Three: Fully aligned with the intent of the mitigation strategy
The maturity level assessment allows organisations to baseline their current state and develop strategies and workplans to uplift their maturity specific to their organisational requirements.
The Essential Eight model is detailed at https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-maturity-model
For further information on Cyber Security assessments and any other services from C5 Technology contact us below;
As part of understanding and actively managing your cyber security threat position, specifically your ability to prevent attacks and limit the impact of any cyber attacks, you should be assessing your organisation’s position against a Cyber Security best practice framework such as NIST or the Australian Government’s Essential 8.
As part of the C5 Technology Cyber Security model, we provide assessments of an organisations Cyber Security position relative to the Essential Eight framework.

Essential Eight
The Essential Eight is an Australian Cyber Security framework developed by the by the Australian Government’s Australian Cyber Security Centre (ACSC). Developed as part of a suite of prioritised strategies to mitigate Cyber Security Incidents and help organisations protect themselves against various cyber threats. The most effective of these mitigation strategies are the Essential Eight.
The framework, published in 2017, with significant updates in July 2021, sets out 8 key security controls that aim to help protect Australian businesses from cyberattacks today.
These eight strategies are divided across three primary objectives – prevent attacks, limit attack impact, and data availability.
- Objective 1: Prevent Cyberattacks
-
- Patch application vulnerabilities
- Application control
- User application hardening
- Configuring MS Office Macro settings
- Objective 2: Limit the Impact of Cyberattacks
-
- Patch operating system vulnerabilities
- Restrict Admin access
- Implement Multi-Factor Authentication (MFA)
- Objective 3: Data Recovery and System Availability
- Daily backups.
The Australian Cyber Security Centre (ACSC) established a three-tier maturity model for the Essential Eight to help businesses protect themselves against cyber threats.
- Maturity Level Zero: Not yet aligned to the intent of the mitigation strategy
- Maturity Level One: Partly aligned with the intent of the mitigation strategy
- Maturity Level Two: Mostly aligned with the intent of the mitigation strategy
- Maturity Level Three: Fully aligned with the intent of the mitigation strategy
The maturity level assessment allows organisations to baseline their current state and develop strategies and workplans to uplift their maturity specific to their organisational requirements.
The Essential Eight model is detailed at https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-maturity-model
For further information on Cyber Security assessments and any other services from C5 Technology contact us below;
